In today’s digital age, wireless networks have become an integral part of our lives. We rely on them for everything from communicating with loved ones to conducting business transactions. However, with the convenience of wireless connectivity comes the risk of unauthorized access by malicious individuals.
Wireless encryption is a crucial security measure that protects our data and ensures the confidentiality of our online activities. But what happens if you need to crack wireless encryption? Whether you’ve forgotten the password to your own network or you want to test the vulnerability of a system, understanding how to crack wireless encryption can be a valuable skill to have. In this article, we will explore various techniques and tools that can be used to crack wireless encryption, as well as the legal and ethical implications of doing so.
Inside This Article
- Understanding Different Types of Wireless Encryption
- Methods to Crack WEP Encryption
- Techniques to Crack WPA/WPA2 Encryption
- Conclusion
- FAQs
Understanding Different Types of Wireless Encryption
When it comes to protecting your wireless network from unauthorized access, encryption plays a vital role. Wireless encryption refers to the process of encoding the transmitted data to ensure that only authorized devices can decipher and access it. By encrypting your wireless network, you can safeguard your sensitive information and prevent hackers from intercepting your data.
There are several types of wireless encryption protocols available, each with its own level of security. It’s important to understand the different types of wireless encryption to make an informed decision about the level of protection you require for your network.
1. Wired Equivalent Privacy (WEP): WEP is the oldest and least secure form of wireless encryption. It uses a 40-bit or 104-bit encryption key to protect data transmission. However, WEP’s vulnerability to various attacks, such as key cracking and packet injection, makes it susceptible to unauthorized access.
2. Wi-Fi Protected Access (WPA): WPA is an improved version of WEP and provides better security measures. It uses a stronger encryption algorithm called TKIP (Temporal Key Integrity Protocol) to secure wireless communication. However, WPA is still prone to dictionary and brute-force attacks.
3. Wi-Fi Protected Access 2 (WPA2): Considered the most secure encryption protocol, WPA2 replaces TKIP with the more robust Advanced Encryption Standard (AES) algorithm. AES uses a 128-bit encryption key, making it significantly more difficult to crack than WEP or WPA. WPA2 is currently the recommended choice for wireless encryption.
4. WPA3: This is the latest encryption standard, providing enhanced security features over WPA2. It uses a stronger encryption algorithm and offers improved protection against brute-force attacks and dictionary attacks. However, WPA3 is relatively new and may not be supported by all devices yet.
Choosing the right encryption protocol for your wireless network depends on various factors, including your device compatibility, network requirements, and security concerns. It is crucial to keep your wireless encryption updated and use the most advanced protocol supported by your devices to ensure maximum security.
By understanding the different types of wireless encryption, you can make an informed decision to protect your wireless network from unauthorized access and safeguard your sensitive information.
Methods to Crack WEP Encryption
WEP (Wired Equivalent Privacy) encryption, once considered a secure method to protect wireless networks, is now known to be vulnerable to various cracking techniques. In this section, we will discuss some common methods used to crack WEP encryption.
1. Brute Force Attack: One of the oldest and simplest methods to crack WEP encryption is through a brute force attack. This involves systematically trying every possible combination of characters until the correct encryption key is found. However, this method can be time-consuming and inefficient, especially for longer encryption keys.
2. Dictionary Attack: A dictionary attack is another commonly used method to crack WEP encryption. It uses a preloaded list of commonly used passwords and phrases to try and match the key. This technique is more efficient than brute force attacks as it narrows down the search by using a predefined list.
3. Aircrack-ng: Aircrack-ng is a popular open-source tool used to crack WEP encryption. It combines the capabilities of packet capture, dictionary attacks, and statistical analysis to recover the WEP key. It utilizes captured data packets to gather enough information and perform key cracking efficiently.
4. KoreK Chopchop: KoreK Chopchop, another technique used to crack WEP encryption, exploits some of the vulnerabilities present in WEP’s RC4 encryption algorithm. By capturing a sufficient number of encrypted packets and manipulating them, KoreK Chopchop can recover the WEP key through statistical analysis.
5. Fragmentation Attack: This method exploits fragmented packets in a WEP-encrypted network to recover the encryption key. By capturing specific pieces of a fragmented packet and analyzing them, an attacker can gain enough information to crack the WEP encryption within a reasonable amount of time.
6. ARP Replay Attack: The Address Resolution Protocol (ARP) replay attack involves capturing legitimate ARP requests and responses from the network and replaying them to confuse the access point and obtain the encryption key. This method can be successful if the access point accepts the replayed ARP packets as valid.
7. WEP Key Cracking Tools: Additionally, there are various tools available, such as Wifite, Fern Wi-Fi Cracker, and Gerix Wi-Fi Cracker, specifically designed to crack WEP encryption. These tools simplify the process by automating the necessary steps and providing a user-friendly interface.
It is important to note that attempting to crack WEP encryption without proper authorization is illegal and unethical. These methods are shared for educational purposes only, to highlight the vulnerabilities of WEP encryption and promote the understanding of wireless security. It is always recommended to use stronger encryption methods, such as WPA/WPA2, to ensure a more secure wireless network.
Techniques to Crack WPA/WPA2 Encryption
Cracking WPA/WPA2 encryption is a more complex task compared to WEP, but with the right tools and techniques, it is still possible. If you are seeking to gain access to a wireless network that uses WPA/WPA2 encryption, here are some techniques you can try:
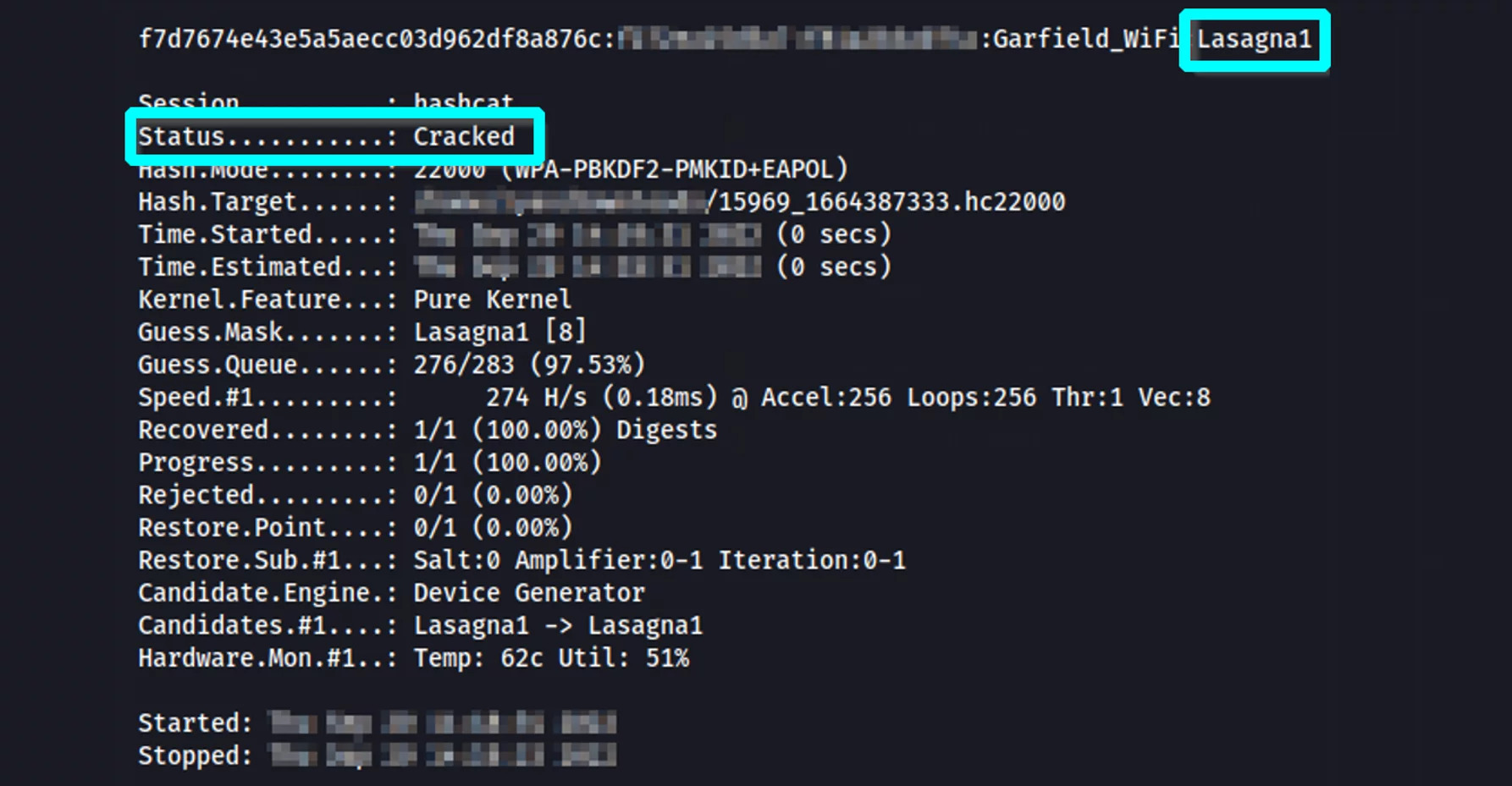
1. Brute Force Attack: One of the common techniques used to crack WPA/WPA2 encryption is a brute force attack. This method involves trying all possible combinations of characters until the correct password is found. Tools like Aircrack-ng and Hashcat can be used for this purpose.
2. Dictionary Attack: Another effective technique is a dictionary attack. In this method, a predefined list of commonly used passwords or a customized wordlist is used to guess the password. Tools like John the Ripper and Pyrit can be used for dictionary attacks.
3. Rainbow Table Attack: A rainbow table is a precomputed table that contains a list of possible plaintext and corresponding encrypted hashes. This technique involves comparing the captured handshake with the entries in the rainbow table to find a match. Tools like oclHashcat and RainbowCrack are commonly used for rainbow table attacks.
4. WPS PIN Attack: If the router has Wi-Fi Protected Setup (WPS) enabled, it may be vulnerable to a WPS PIN attack. This method involves guessing the eight-digit WPS PIN, which can eventually lead to cracking the WPA/WPA2 encryption. Tools like Reaver and Bully are commonly used for WPS PIN attacks.
5. Evil Twin Attack: An evil twin attack involves creating a fake wireless access point that mimics the target network. When users connect to the fake network, their traffic can be intercepted, and the WPA/WPA2 passphrase can be captured. Tools like Karma and Fluxion can be used for evil twin attacks.
It’s important to note that attempting to crack WPA/WPA2 encryption without proper authorization is illegal. These techniques should only be used for educational purposes or with explicit permission from the network owner.
Remember to always protect your own network with a strong WPA/WPA2 passphrase to prevent unauthorized access and ensure the security of your data.
Conclusion
Cracking wireless encryption may seem like a daunting task, but with the right tools and knowledge, it can be accomplished. In this article, we have explored the various methods and techniques used to crack wireless encryption, including Wi-Fi hacking tools, brute force attacks, and vulnerabilities in encryption protocols.
However, it is important to note that attempting to crack wireless encryption without the permission of the network owner is illegal and unethical. This article is intended for educational purposes only, to understand the vulnerabilities in wireless networks and take necessary measures to secure our own networks.
By understanding the weaknesses in wireless encryption and implementing strong security measures, such as using WPA2 encryption, regularly updating passwords, and monitoring network activity, we can protect our wireless networks from unauthorized access.
Remember, cybersecurity is a constantly evolving field, and staying updated with the latest encryption protocols and security measures is crucial for maintaining the privacy and security of our wireless networks.
FAQs
1. What is wireless encryption?
Wireless encryption is a security measure used to protect wireless networks from unauthorized access. It involves encoding the transmitted data in a way that can only be decrypted with a specific key or passphrase.
2. Why is wireless encryption important?
Wireless encryption is important because it helps secure your wireless network and prevent unauthorized users from accessing your network or intercepting your data. It ensures that your communication and information remain private and protected.
3. What are the different types of wireless encryption?
There are several types of wireless encryption protocols, including WEP (Wired Equivalent Privacy), WPA (Wi-Fi Protected Access), and WPA2 (Wi-Fi Protected Access 2). WPA2 is currently the most secure and widely used encryption protocol.
4. Can wireless encryption be cracked?
While no encryption method is completely foolproof, some wireless encryption protocols are more vulnerable to cracking than others. Older protocols like WEP are relatively easy to crack, while newer protocols like WPA2 are much more secure and resistant to cracking attempts.
5. How can I strengthen my wireless network security?
To strengthen your wireless network security, ensure that you are using the latest and most secure encryption protocol, such as WPA2. Additionally, you should choose a strong and unique password for your network, regularly update your wireless router’s firmware, and disable any unnecessary network features or services that could be potential security risks.
