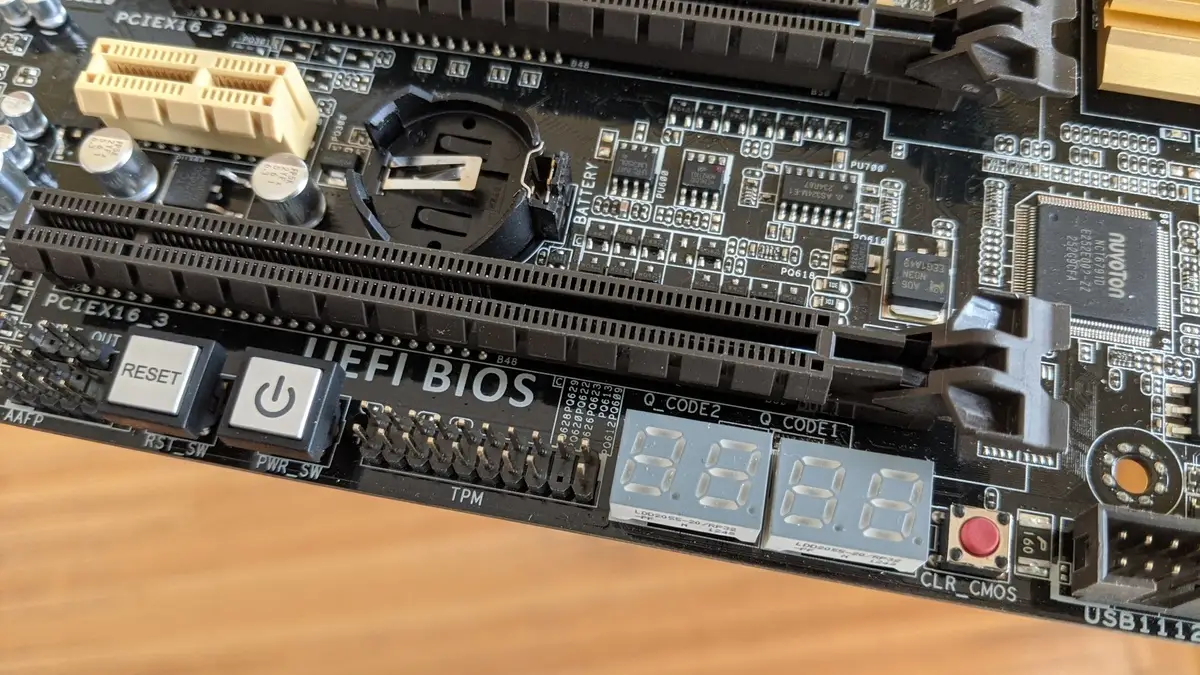
When it comes to building or upgrading a computer, one of the key components that often goes overlooked is the TPM connector on the motherboard. While many users are familiar with various connectors and ports on motherboards, the TPM connector may be unfamiliar territory for some.
TPM stands for Trusted Platform Module, which is a chip on the motherboard that provides hardware-based security features. It adds an extra layer of protection to the computer by securely storing encryption keys, passwords, and other sensitive data. The TPM connector allows for the connection of a TPM module, which is a small add-on board that contains the TPM chip.
In this article, we will delve into the details of what a TPM connector is, its purpose, and why it is important for computer security. Whether you are a tech enthusiast looking to understand the inner workings of your computer or a beginner building your first PC, this article will provide you with the information you need.
Inside This Article
- TPM 2.0 Overview
- Role and Purpose of a TPM Connector
- Compatibility and Installation of TPM Connector
- Benefits and Applications of TPM Connector
- Conclusion
- FAQs
TPM 2.0 Overview
TPM 2.0, which stands for Trusted Platform Module 2.0, is a hardware-based security feature that is integrated into modern computer systems, particularly motherboards. It serves as a dedicated chip that provides critical security functions to protect sensitive data, authenticate hardware components, and establish a secure platform for various cryptographic operations.
TPM 2.0 offers enhanced security capabilities compared to its predecessor, TPM 1.2. It provides a more robust and flexible framework for securing the system against unauthorized access, tampering, and data breaches. With TPM 2.0, users can benefit from advanced encryption algorithms, remote attestation, sealed storage, and secure key management.
One of the key advancements of TPM 2.0 is its support for cryptographic agility. This means that it can adapt to evolving security standards and algorithms, ensuring the long-term viability and compatibility of the security platform. TPM 2.0 also introduces stronger identity capabilities, enabling secure identification and authentication of hardware components, software, and users.
TPM 2.0 is designed to work seamlessly with various operating systems, including Windows, Linux, and macOS. It is integrated into the motherboard and communicates directly with the system firmware. This integration ensures that the TPM functions are available right from the system boot process, providing a secure foundation for the entire system to operate upon.
With the increasing number of cyber threats and data breaches, TPM 2.0 plays a crucial role in protecting sensitive information such as encryption keys, digital certificates, and credentials. It can help secure the boot process, protect the integrity of the operating system, and safeguard data stored on the system.
Overall, TPM 2.0 is a powerful security feature that enhances the trustworthiness and integrity of computer systems. It provides a foundation for secure operations, enables advanced cryptographic functions, and ensures the confidentiality and integrity of sensitive data. By leveraging TPM 2.0, users can have peace of mind knowing that their systems are protected by state-of-the-art security measures.
Role and Purpose of a TPM Connector
A Trusted Platform Module (TPM) connector plays a crucial role in enhancing the security features of a motherboard. It serves as a dedicated hardware component that aids in the implementation of cryptographic functions and secure storage of sensitive data. The primary purpose of a TPM connector is to provide a secure and tamper-resistant environment for key generation, storage, and management.
One of the key roles of a TPM connector is to enable the motherboard to support the TPM standard, which ensures the integrity of the system and protects against various cyber threats. The TPM connector acts as an interface that allows a TPM module to be connected to the motherboard, thus expanding its security capabilities.
By incorporating a TPM connector on a motherboard, users can take advantage of advanced security features such as secure boot, device encryption, and secure login. The TPM module, when connected to the motherboard via the TPM connector, enhances the overall security posture of the system by providing trusted computing functionalities.
With the TPM connector, the motherboard can communicate with the TPM module, allowing for the secure generation and management of cryptographic keys. These keys are used for encryption and decryption processes, securing important data and preventing unauthorized access.
Moreover, the TPM connector facilitates the storage of passwords, certificates, and other sensitive information on the TPM module. This secure storage feature helps protect private data from being compromised or tampered with by malicious actors.
In addition to its role in enhancing security, the TPM connector can also enable hardware-based attestation, which allows the system to validate its integrity and verify its configuration. This feature is especially valuable in enterprise environments where maintaining the security and trustworthiness of systems is of utmost importance.
Overall, the role and purpose of a TPM connector on a motherboard is to provide an additional layer of security, enabling the implementation of robust cryptographic functions, secure storage, and hardware-based attestation. By utilizing a TPM connector, users can enhance the security capabilities of their systems and protect sensitive data from unauthorized access and tampering.
Compatibility and Installation of TPM Connector
When it comes to the compatibility and installation of a TPM connector on a motherboard, there are a few factors to consider. Let’s dive into the details to understand how this crucial component can be seamlessly integrated into your system.
1. Compatibility:
The first step is to ensure that your motherboard supports a TPM connector. Check the specifications or product documentation of your motherboard to verify if it has a TPM header or slot. Most modern motherboards have a dedicated TPM connector to accommodate a TPM module.
2. TPM Module:
Once you have confirmed the compatibility, the next step is to acquire a TPM module. These modules are small chips that contain the necessary firmware and cryptographic functions. Make sure to purchase a TPM module that is compatible with your motherboard and supports the TPM version required.
3. Physical Installation:
Installing the TPM module onto the TPM connector is a relatively straightforward process. Locate the TPM header on your motherboard; it is usually labeled as “TPM” or “TPM Header.” Align the pins on the TPM module with the holes on the TPM connector, ensuring a proper connection.
4. Software Configuration:
Once the TPM module is physically installed, you need to configure it through your system’s BIOS settings. Access the BIOS menu by pressing a specific key during system startup (usually F2 or Delete). Look for the TPM-related settings in the BIOS and enable the TPM functionality.
5. Operating System Support:
After the TPM module is installed and enabled, you may need to install specific software or drivers to utilize its full capabilities. Check the manufacturer’s website for any necessary software updates or drivers that are compatible with your operating system.
6. Verify Functionality:
Once everything is set up, it’s essential to verify the functionality of the TPM module. This can be done through various means, such as using the manufacturer’s diagnostic tool or checking the BIOS settings for TPM status and version.
Remember to refer to the motherboard or TPM module’s documentation for detailed instructions specific to your hardware. Following these steps will ensure a successful installation and compatibility of the TPM connector on your motherboard.
Benefits and Applications of TPM Connector
The TPM (Trusted Platform Module) connector on a motherboard offers a range of benefits and enables various applications that enhance the security and functionality of a computer system. Let’s explore some of the key advantages and use cases of a TPM connector.
1. Enhanced System Security:
One of the primary benefits of a TPM connector is the ability to enhance system security. A TPM module can securely store encryption keys, digital certificates, and other sensitive data, providing a hardware-based trusted platform for secure computing. This helps protect against unauthorized access, tampering, and data breaches.
2. Secure Boot and Remote Attestation:
By utilizing a TPM connector, the system can support secure boot, which ensures the integrity of the boot process and protects against bootkit attacks. Additionally, TPM enables remote attestation, allowing trusted verification of the system’s integrity to external entities. This is particularly important in environments where secure communication and data integrity are essential.
3. Password Protection and Device Authentication:
A TPM connector enables the implementation of advanced security features such as password protection and device authentication. By utilizing TPM, users can protect their devices with strong passwords and implement two-factor authentication methods, improving overall system security and preventing unauthorized access.
4. Data Encryption and Secure Storage:
Another valuable application of a TPM connector is its support for data encryption and secure storage. The TPM module can generate, store, and manage encryption keys, facilitating efficient and secure encryption of sensitive data. This is particularly crucial for safeguarding personal information, financial data, and other confidential files.
5. Compliance with Security Standards:
Many industries and organizations have strict security standards and regulations. By utilizing a TPM connector, computer systems can comply with these requirements more effectively. TPM offers a hardware-based security solution that helps meet the stringent compliance criteria, ensuring data protection and integrity.
6. Trusted Execution Environment:
TPM connectors enable the creation of a trusted execution environment within the system. This environment helps isolate and protect critical processes, creating a secure space for running sensitive applications, such as secure online transactions, digital rights management, and virtual private networks (VPNs).
Conclusion
In conclusion, the TPM connector on a motherboard plays a crucial role in ensuring the security and integrity of a computer system. It allows for the integration of a Trusted Platform Module, a specialized security chip that enhances the protection of sensitive data and prevents unauthorized access.
By connecting a TPM module to the motherboard, users can benefit from features such as secure boot, encryption, and remote attestation. These capabilities are especially important in today’s digital landscape, where cyber threats are constantly evolving.
Whether you’re a tech enthusiast or a professional looking to build a secure system, understanding the TPM connector and its implications is essential. By implementing this advanced security feature, you can safeguard your data, mitigate the risk of attacks, and have peace of mind knowing that your confidential information is protected.
So, the next time you’re evaluating a motherboard for your computer build, don’t forget to check if it has a TPM connector or if it supports TPM modules. Your data security will thank you for it!
FAQs
Here are some frequently asked questions about the TPM connector on a motherboard:
Q: What is a TPM connector on a motherboard?
A: A TPM (Trusted Platform Module) connector is a dedicated port on a motherboard that allows for the installation of a TPM module. This module is a specialized chip that adds an extra layer of security to a computer system by providing cryptographic functions and secure storage for encryption keys, passwords, and other sensitive data.
Q: Why is a TPM connector important?
A: The TPM connector is important because it allows for the integration of a TPM module, which plays a crucial role in enhancing the security of a computer system. With a TPM module installed, users can benefit from features like secure boot, encryption support, and hardware-based authentication, protecting their data and system from unauthorized access and tampering.
Q: Can I add a TPM module if my motherboard doesn’t have a TPM connector?
A: If your motherboard doesn’t have a TPM connector, it is generally not possible to add a TPM module directly. However, some motherboards may offer alternatives, such as the ability to add a TPM module via USB or other expansion slots. It’s important to consult your motherboard’s documentation or manufacturer to determine if such options are available.
Q: How do I identify the TPM connector on my motherboard?
A: The location and appearance of the TPM connector can vary depending on the motherboard’s manufacturer and model. However, it is typically a 20 or 24-pin header found near the edge of the motherboard. Consult your motherboard’s user manual or manufacturer’s website for specific instructions on identifying the TPM connector on your motherboard.
Q: What are some common uses of a TPM module?
A: A TPM module can be used for various purposes, including secure storage of encryption keys for full disk encryption or BitLocker, facilitating hardware-based authentication for secure login processes, enhancing secure boot capabilities, and supporting digital rights management (DRM) functionalities. It is particularly useful in business and enterprise environments where data security is of utmost importance.
