Are you concerned about the security of your wireless network? Do you want to know who is connected to your network and monitor their activity? If so, you’ve come to the right place! In this article, we will explore how you can effectively monitor the activity on your wireless network and ensure the safety of your data.
With the increasing reliance on wireless networks, it becomes crucial to keep a close eye on the devices that are connected to your network. Whether it’s to protect your personal information or to prevent unauthorized access, monitoring network activity is a vital aspect of maintaining a secure digital environment.
In the following sections, we will discuss various methods and tools that can help you monitor the activity on your wireless network. From using built-in features on your router to utilizing third-party applications, we will cover everything you need to know to keep your network secure. So, let’s dive in and learn how to gain control over your wireless network’s activity!
Inside This Article
- Why Monitor Activity on Your Wireless Network?
- Different Methods to Monitor Activity on Your Wireless Network
- Router Logs
- Network Monitoring Software
- MAC Address Filtering
- Analyzing Network Traffic
- Conclusion
- FAQs
Why Monitor Activity on Your Wireless Network?
Monitoring activity on your wireless network is crucial for various reasons. In today’s digital age, where most of our personal and professional lives depend on the internet, it is essential to ensure the security and performance of your network. Here are a few reasons why monitoring your wireless network activity is important:
1. Security: One of the primary reasons to monitor activity on your wireless network is to protect it from unauthorized access. By keeping track of the devices connected to your network, you can quickly identify any unknown or suspicious devices that may be attempting to gain access to your network.
2. Bandwidth Consumption: Monitoring network activity allows you to identify devices or applications that are consuming excessive bandwidth. By pinpointing these bandwidth hogs, you can take appropriate action to optimize your network’s performance and ensure a smooth internet experience for all users.
3. Malware Detection: Monitoring network activity also helps in detecting any malware or malicious activities occurring within your network. Unusual or suspicious data traffic patterns can indicate the presence of malware-infected devices or potential security breaches. By identifying and addressing these threats promptly, you can safeguard your network from potential harm.
4. Parental Controls: If you have children or other vulnerable users accessing your wireless network, monitoring activity becomes even more crucial. By monitoring the websites visited and applications used, you can ensure that the internet usage is appropriate and safe for everyone in your household.
5. Compliance and Legal Requirements: Depending on your industry or jurisdiction, you may have specific compliance or legal requirements regarding the usage and security of your wireless network. Monitoring activity allows you to meet these obligations, keep track of user access, and ensure that your network is in compliance with relevant regulations.
Overall, monitoring activity on your wireless network provides you with the necessary insights to maintain network security, optimize performance, and ensure compliance with legal and industry requirements. By actively monitoring your network, you can proactively address any issues, mitigate risks, and provide a safe and reliable internet experience for all users.
Different Methods to Monitor Activity on Your Wireless Network
Monitoring the activity on your wireless network is essential to ensure its security and optimize its performance. By keeping a close eye on the devices connected to your network and the data being transmitted, you can identify any unauthorized access or suspicious activities. In this article, we will explore some different methods you can use to effectively monitor the activity on your wireless network.
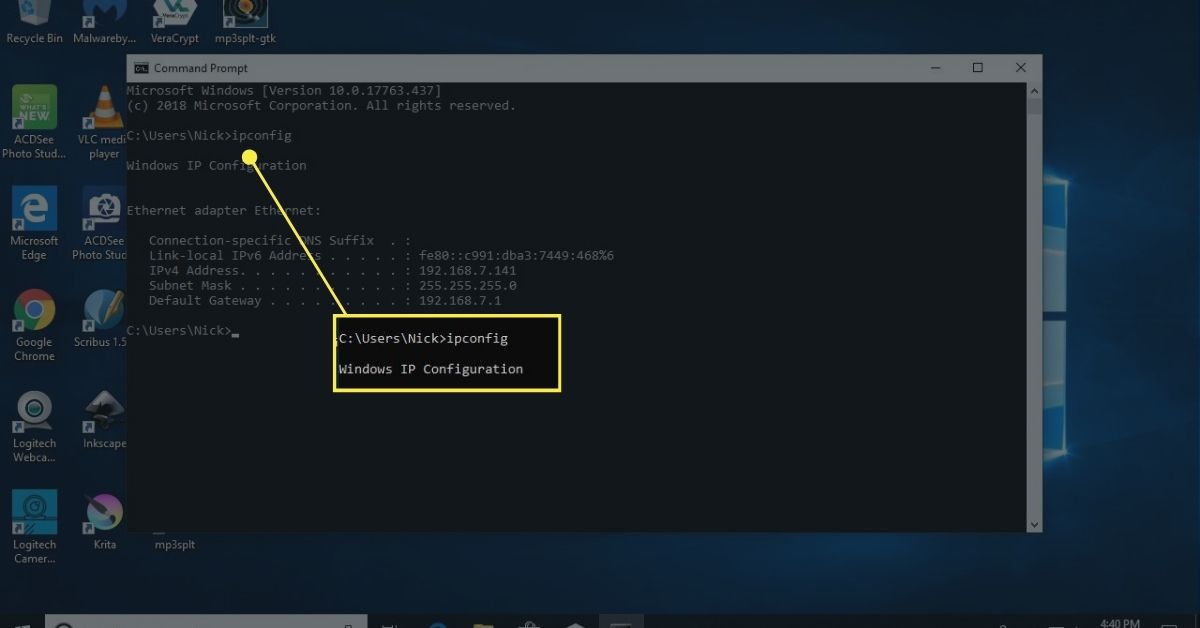
1. Router Logs: Many routers provide built-in logging features that can help you monitor network activity. These logs record important information such as the devices connected to your network, the websites visited, and the data transmitted. By accessing the router’s settings, you can review these logs and look for any unusual or suspicious activity.
2. Network Monitoring Software: Another effective method to monitor your wireless network activity is by using network monitoring software. These tools allow you to monitor all the devices connected to your network, track their bandwidth usage, and detect any unauthorized access attempts. Network monitoring software often provides real-time monitoring, alerts, and detailed reports to help you better understand your network activity.
3. MAC Address Filtering: MAC address filtering is a method that allows you to control which devices can connect to your wireless network based on their unique MAC addresses. By configuring your router to only allow specific MAC addresses, you can prevent unauthorized devices from accessing your network. Monitoring MAC address filtering can help you identify any unknown or unauthorized devices attempting to connect.
4. Analyzing Network Traffic: Monitoring network traffic can provide valuable insights into the activity on your wireless network. By using network analysis tools, you can examine the data packets being transmitted, identify the source and destination of the traffic, and analyze the protocols used. This method allows you to detect any suspicious or unusual network activity, such as large data transfers or unauthorized access attempts.
Monitoring the activity on your wireless network is vital to maintain its security and performance. By employing these different methods, you can stay vigilant and ensure that only authorized devices are connected to your network, while identifying any potential threats or vulnerabilities. Remember to regularly check the logs, use network monitoring software, implement MAC address filtering, and analyze network traffic to keep your wireless network safe and secure.
Router Logs
Router logs are a vital tool for monitoring activity on your wireless network. Every time a device connects to your router or performs any network-related activity, it generates a log entry. These logs contain valuable information such as the IP address, MAC address, and timestamp of the activity.
To access the router logs, you need to log in to your router’s administrative interface. The exact procedure may vary depending on your router model, but it typically involves opening a web browser and entering the router’s IP address.
Once logged in, you will find a section dedicated to router logs. Here, you can view and analyze the logs to gain insights into the devices connected to your network and their activity.
The router logs provide a chronological record of all network events, including device connections, disconnections, and data transfers. By reviewing these logs, you can identify any suspicious or unauthorized activities on your network.
It’s important to note that router logs may be limited in terms of the amount of detail they provide. While they are valuable for basic monitoring, they may not provide more granular information about the nature of the network traffic or the specific websites visited by devices on your network.
It is recommended to regularly check your router logs to stay updated on the activity happening on your wireless network. By doing so, you can ensure the security and optimal performance of your network.
Network Monitoring Software
Another effective method to monitor activity on your wireless network is by using network monitoring software. This software provides you with detailed insights into the devices connected to your network, the amount of data they are consuming, and the types of activities they are engaged in.
Network monitoring software allows you to set up alerts and notifications whenever any suspicious or unauthorized activity is detected on your network. This can include unusual data transfers, multiple login attempts, or the presence of unidentified devices.
With network monitoring software, you can also track the bandwidth usage of individual devices on your network. This information can be useful in identifying any devices or users that are hogging a significant portion of your network’s bandwidth, potentially causing slowdowns for other users.
Furthermore, network monitoring software often includes features such as traffic analysis and protocol monitoring. These features allow you to analyze the incoming and outgoing data traffic on your network, giving you visibility into the types of websites or applications being accessed.
This type of software typically offers user-friendly dashboards and reports that make it easy to understand and interpret the network data. It also allows you to customize the monitoring parameters according to your specific requirements.
One popular network monitoring software is PRTG Network Monitor. PRTG offers a wide range of monitoring functionalities, including real-time monitoring, customizable alerts, and comprehensive reporting. It supports various protocols and provides detailed insights into your network’s performance and activity.
When selecting network monitoring software, it is important to consider factors such as ease of use, compatibility with your network configuration, and the level of support provided. Additionally, ensure that the software adheres to industry security standards to protect your network data.
By utilizing network monitoring software, you can have peace of mind knowing that your wireless network is being actively monitored and any suspicious activity can be detected and addressed promptly.
MAC Address Filtering
One effective method to monitor activity on your wireless network is by using MAC address filtering. MAC addresses are unique identifiers assigned to network devices, such as smartphones, laptops, and tablets. By enabling MAC address filtering on your router, you can control which devices are allowed to connect to your network.
To implement MAC address filtering, you need to access your router’s settings. Typically, this can be done by typing the router’s IP address into a web browser and entering the login credentials. Once you’re logged in, you can locate the MAC address filtering settings.
When setting up MAC address filtering, you have two options: allow or deny. If you choose to allow, only devices with specific MAC addresses listed in your router’s settings will be able to connect to the network. This can provide an extra layer of security, preventing unauthorized devices from accessing your network.
If you opt for deny mode, you can block specific MAC addresses from connecting to your network. This can be useful if there are certain devices you want to restrict or if you suspect unauthorized access from a particular MAC address.
MAC address filtering works by comparing the MAC address of a device attempting to connect to the network with the list of allowed or blocked MAC addresses. If the address matches an entry in the list, the device is either granted or denied access accordingly.
While MAC address filtering can help you monitor and control the devices connecting to your network, it is important to note that MAC addresses can be spoofed or falsified. This means that determined hackers or individuals with malicious intent may still be able to bypass this security measure.
Despite its limitations, MAC address filtering can be a valuable tool in monitoring and managing activity on your wireless network. By utilizing this feature, you can have greater control over the devices allowed to connect, enhancing the security and performance of your network.
Analyzing Network Traffic
Analyzing network traffic is a crucial method to monitor activity on your wireless network. By examining the data packets flowing through the network, you can gain valuable insights into the devices connected, the websites accessed, and the data transferred.
There are several tools and techniques you can use to analyze network traffic. One commonly used method is to employ a network analyzer or packet sniffer. These tools intercept and capture network packets, allowing you to examine their contents and understand the communication happening on your network.
Network analyzers provide detailed information about the source and destination IP addresses, protocols used, ports accessed, and even the size of the data packets. This information can help you identify any suspicious or unauthorized activity taking place on your wireless network.
Another approach to analyzing network traffic is to use intrusion detection and prevention systems (IDPS). These systems monitor network traffic in real-time, looking for any signs of malicious activity or unauthorized access attempts. They can alert you to potential security threats and help you take the necessary steps to protect your network.
You can also utilize traffic analysis tools that provide visual representations of network traffic patterns. These tools help you identify any spikes or anomalies in data usage, enabling you to investigate further and pinpoint any potential issues or unauthorized activities.
Remember, monitoring network traffic requires technical expertise and the right tools. It’s advisable to consult with IT professionals or consider hiring a network security specialist to assist you with the analysis, interpretation, and implementation of appropriate security measures.
Conclusion
In conclusion, monitoring activity on your wireless network is a crucial step in ensuring its security and optimizing its performance. By staying vigilant and regularly checking for any suspicious or unauthorized activities, you can safeguard your network from potential threats and maintain its efficiency.
Implementing effective monitoring tools and techniques, such as using network monitoring software or configuring your router’s settings, allows you to keep track of the devices connected to your network, track data usage, and identify any unusual behaviors or unauthorized access attempts.
Remember, the security of your wireless network is in your hands. By staying informed and proactive, you can protect your sensitive information, prevent unauthorized access, and enjoy a seamless and secure wireless experience.
So, take the necessary steps to monitor your wireless network and stay one step ahead of potential risks. Your peace of mind and network security will be well worth the effort.
FAQs
1. Why is it important to monitor activity on my wireless network?
Monitoring activity on your wireless network is crucial for several reasons. Firstly, it helps you identify any unauthorized access or suspicious activity that could potentially compromise the security of your network and personal information. By keeping an eye on network activity, you can detect and prevent any potential cyber threats, such as hacking attempts or unauthorized devices connecting to your network.
2. How can I monitor activity on my wireless network?
There are several ways to monitor activity on your wireless network. One of the most common methods is by accessing your router’s admin panel. From there, you can typically find a section that displays a list of connected devices and their activity. Additionally, you can use network monitoring software or mobile apps specifically designed for monitoring network activity. These tools provide more detailed information about the devices connected to your network and their respective activity, allowing you to track and analyze network usage.
3. What should I look for when monitoring activity on my wireless network?
When monitoring activity on your wireless network, there are a few key things to look out for. Firstly, check for any unfamiliar or unknown devices connected to your network. This could indicate an unauthorized user attempting to gain access. You should also keep an eye out for any excessive or unusual data usage patterns, as this could potentially indicate a compromised device or a device engaging in malicious activities. Lastly, monitor for any suspicious network traffic or unusual connection attempts.
4. What steps can I take if I detect suspicious activity on my wireless network?
If you detect suspicious activity on your wireless network, it’s important to take immediate action to protect your network and personal information. Start by changing the Wi-Fi password to prevent further unauthorized access. You may also consider enabling MAC address filtering, which allows only specific devices to connect to your network. Furthermore, running antivirus and malware scans on your devices can help detect and remove any potential threats. If the issue persists, it may be advisable to contact your internet service provider or a professional IT expert for further assistance.
5. How frequently should I monitor activity on my wireless network?
The frequency of monitoring activity on your wireless network depends on your personal preference and the level of security you require. As a general guideline, it’s recommended to check the status of your network and its connected devices at least once a month. However, if you run a business or have sensitive data on your network, you may want to monitor it more frequently, such as once a week or even daily. Regular monitoring helps ensure that you can promptly address any potential security issues and maintain a secure network environment.
