In today's interconnected world, the ability to access another mobile device using an IP address has become increasingly valuable. Whether for troubleshooting, remote assistance, or file sharing, understanding how to utilize IP addresses to connect to another mobile device can be a game-changer. This article will guide you through the process of accessing another mobile using an IP address, providing valuable insights and practical tips to ensure a seamless and secure connection. From understanding the basics of IP addresses to implementing effective methods for remote access, this comprehensive guide will equip you with the knowledge and skills needed to navigate the world of mobile connectivity with confidence. So, let's dive in and explore the fascinating realm of accessing another mobile using an IP address.
Inside This Article
- Understanding IP Address
- Using IP Address to Access Another Mobile
- Precautions and Security Measures
- Conclusion
- FAQs
Understanding IP Address
An IP address, or Internet Protocol address, is a unique string of numbers separated by periods that identifies each device using the Internet Protocol to communicate over a network. It serves as a digital address, allowing devices to locate and communicate with each other. IP addresses are essential for enabling data transmission and ensuring that information reaches its intended destination accurately and efficiently.
There are two primary types of IP addresses: IPv4 and IPv6. IPv4 addresses consist of four sets of numbers ranging from 0 to 255, such as 192.168.1.1, while IPv6 addresses are longer and more complex, often represented as a series of hexadecimal digits and colons. As the demand for IP addresses continues to grow with the increasing number of connected devices, IPv6 has been developed to provide a larger pool of available addresses.
IP addresses are allocated to devices dynamically or statically. Dynamic IP addresses are assigned by a network's Dynamic Host Configuration Protocol (DHCP) server and may change over time, while static IP addresses are manually configured and remain constant.
Moreover, IP addresses are categorized into public and private addresses. Public IP addresses are globally unique and are assigned to devices directly connected to the internet, allowing them to be identified and accessed from anywhere in the world. On the other hand, private IP addresses are used within a local network and are not accessible from the internet. They enable devices within the same network to communicate with each other while sharing a single public IP address for external communication.
Understanding IP addresses is crucial for various networking tasks, including accessing another mobile device using its IP address. By grasping the fundamentals of IP addressing, individuals can navigate the intricacies of network communication and leverage this knowledge to establish connections, troubleshoot connectivity issues, and optimize network performance.
Using IP Address to Access Another Mobile
Accessing another mobile device using its IP address can be a valuable capability in various scenarios, such as remote troubleshooting, file sharing, or accessing resources on a different network. However, it's important to note that accessing another mobile device using its IP address typically requires both devices to be connected to the same local network, as public IP addresses are generally not directly accessible due to network address translation (NAT) and firewall configurations.
Here are the steps to access another mobile device using its IP address:
-
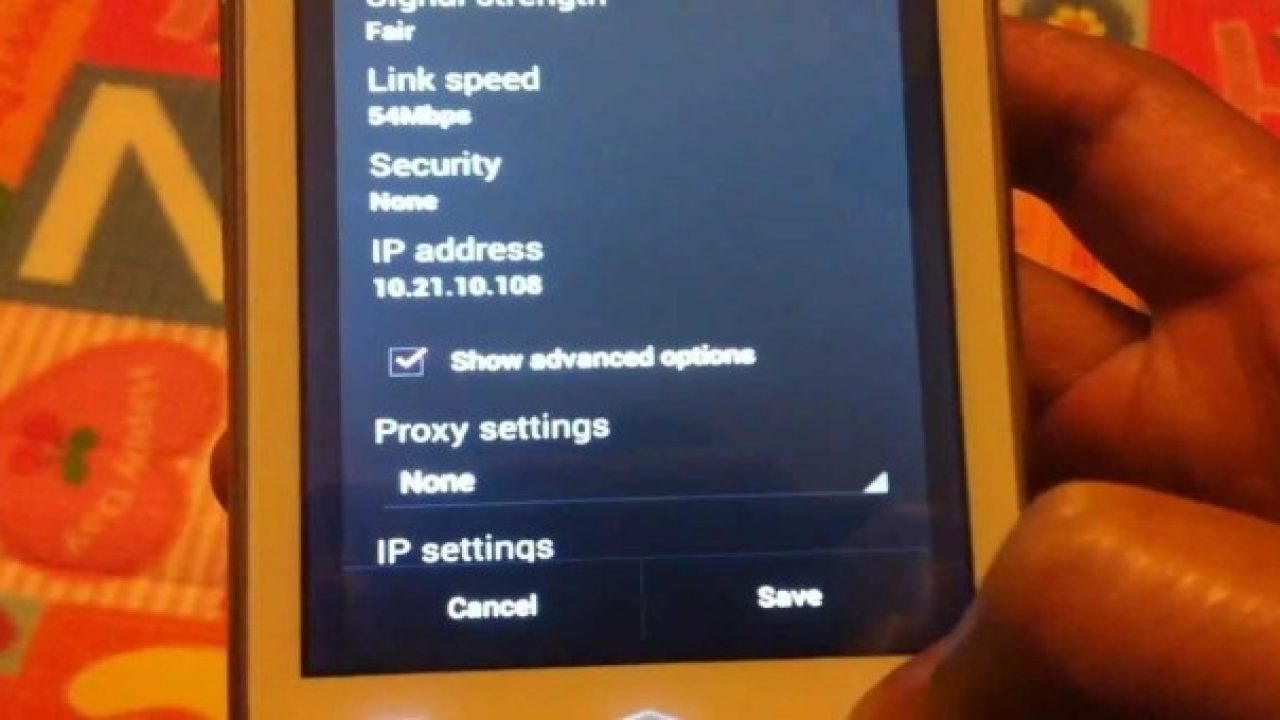
Determine the Target Device's IP Address: The first step is to identify the IP address of the mobile device you want to access. On Android devices, you can find this information by navigating to Settings > Wi-Fi, selecting the connected network, and then viewing the device's IP address. On iOS devices, the IP address can be found in Settings > Wi-Fi > (i) next to the connected network.
-
Enable Remote Access: Depending on the purpose of accessing the other mobile device, you may need to enable remote access features such as Remote Desktop or SSH (Secure Shell) on the target device. These features allow for secure and controlled access to the device's interface or command line.
-
Use Remote Access Tools: Once the target device's IP address is known and remote access is enabled, you can use appropriate remote access tools to establish a connection. For example, Remote Desktop Protocol (RDP) or Virtual Network Computing (VNC) applications can be used to access the graphical interface of the target device, while SSH clients provide command-line access.
-
Authentication and Security: When accessing another mobile device using its IP address, it's crucial to prioritize security. Utilize strong, unique passwords for remote access, and consider using virtual private network (VPN) connections for added security, especially when accessing devices over public networks.
-
Network Configuration: Ensure that the local network allows for the necessary traffic to pass through, and consider configuring port forwarding on the router if accessing the device from an external network.
It's important to emphasize that accessing another mobile device using its IP address should be done responsibly and with the consent of the device owner. Additionally, understanding the potential security risks and implementing appropriate security measures is essential to safeguard the privacy and integrity of the accessed device and the network as a whole.
By following these steps and considering the associated security implications, individuals can effectively utilize IP addresses to access other mobile devices within a network, enabling seamless collaboration and troubleshooting while maintaining a strong focus on security and privacy.
Precautions and Security Measures
When accessing another mobile device using its IP address, it is imperative to prioritize security and implement precautionary measures to mitigate potential risks. While the ability to access a mobile device remotely can offer convenience and facilitate collaboration, it also introduces security vulnerabilities that must be addressed proactively. By adhering to best practices and implementing robust security measures, individuals can safeguard both the accessed device and the overall network from unauthorized access and potential exploitation.
Strong Authentication and Access Control
One of the fundamental precautions when accessing another mobile device via its IP address is to enforce strong authentication mechanisms. This involves utilizing complex, unique passwords or passphrase-based authentication to prevent unauthorized access. Additionally, implementing multi-factor authentication (MFA) further fortifies the access control by requiring multiple forms of verification, such as a password combined with a one-time code sent to a trusted device.
Encryption and Secure Communication
To protect the confidentiality and integrity of data transmitted during remote access, it is essential to employ encryption protocols. Utilizing secure communication channels, such as SSL/TLS for web-based access or SSH for command-line access, ensures that the data exchanged between the accessing device and the target mobile device remains encrypted and resistant to eavesdropping or tampering.
Network Segmentation and Access Restrictions
Implementing network segmentation and access restrictions within the local network environment can bolster security when accessing mobile devices via their IP addresses. By segregating devices into distinct network segments and enforcing access control policies, the impact of a potential security breach can be limited, and unauthorized access attempts can be mitigated through granular control over network traffic.
Regular Security Updates and Patch Management
Maintaining the security posture of the accessed mobile device is crucial in mitigating known vulnerabilities and safeguarding against potential exploits. Regularly updating the mobile device's operating system, applications, and security software helps to address security flaws and vulnerabilities, reducing the risk of exploitation by malicious actors seeking to compromise the device through known weaknesses.
Monitoring and Logging
Enabling comprehensive monitoring and logging capabilities on the accessed mobile device and the network infrastructure facilitates the detection of suspicious activities and unauthorized access attempts. By reviewing logs and monitoring network traffic, anomalous behavior can be identified, allowing for timely response and mitigation of potential security incidents.
Consent and Ethical Considerations
Respect for privacy and ethical considerations should underpin the practice of accessing another mobile device using its IP address. It is essential to obtain explicit consent from the device owner before initiating remote access, ensuring that the access is conducted within legal and ethical boundaries. Transparency and clear communication regarding the purpose and duration of access contribute to fostering trust and maintaining ethical conduct.
By integrating these precautions and security measures into the process of accessing another mobile device via its IP address, individuals can establish a secure and responsible approach to remote access. Prioritizing security, privacy, and ethical considerations not only safeguards the integrity of the accessed device and the network but also fosters a culture of responsible and conscientious remote device management.
In conclusion, accessing another mobile using an IP address can be a useful and practical solution for various scenarios. Whether it's for troubleshooting, remote assistance, or file sharing, understanding how to utilize IP addresses to connect to another mobile device can greatly enhance productivity and convenience. By following the appropriate steps and ensuring the necessary permissions are in place, users can establish a secure and efficient connection between devices. This capability opens up a world of possibilities for collaboration and support, making it a valuable skill for anyone seeking to maximize the potential of their mobile devices.
FAQs
-
Can I Access Another Mobile Using Its IP Address?
- Yes, it is possible to access another mobile device using its IP address. However, it's important to note that this typically requires advanced technical knowledge and may not be legal or ethical in certain situations. Always ensure that you have proper authorization and adhere to legal and ethical guidelines when attempting to access another mobile device using its IP address.
-
What Are the Legal Implications of Accessing Another Mobile Using Its IP Address?
- Accessing another mobile device using its IP address without proper authorization can potentially violate privacy laws and cybersecurity regulations. It's crucial to understand the legal implications and seek legal advice if you are unsure about the legality of accessing another mobile device in this manner.
-
Is It Safe to Access Another Mobile Using Its IP Address?
- Accessing another mobile device using its IP address can pose significant security risks, including potential exposure to malicious attacks and unauthorized access to sensitive information. It's essential to prioritize cybersecurity and only attempt to access another mobile device using its IP address within legal and ethical boundaries.
-
What Are the Common Methods for Accessing Another Mobile Using Its IP Address?
- Common methods for accessing another mobile device using its IP address include remote desktop applications, network scanning tools, and exploiting vulnerabilities in the target device's network configuration. However, it's important to emphasize that these methods should only be employed for legitimate and authorized purposes.
-
How Can I Protect My Mobile Device from Unauthorized Access via IP Address?
- To protect your mobile device from unauthorized access via IP address, it's crucial to implement robust security measures such as using a strong password, enabling two-factor authentication, keeping the device's software updated, and utilizing a reputable virtual private network (VPN) for secure connections. Additionally, being cautious about sharing your IP address and avoiding suspicious links and downloads can further enhance your device's security.
