In today’s digital age, mobile phones have become an integral part of our lives. They hold our contacts, messages, photos, and other sensitive information. With the increasing reliance on smartphones, it is crucial to ensure that our devices are secure from potential threats and vulnerabilities. One important aspect of mobile phone security is the keychain, which stores passwords and other sensitive data.
But how can we ensure that our keychain is secure? And what steps can we take to fix any security risks that may arise? In this article, we will delve into the world of keychain security recommendations for mobile phones. We will explore the importance of a secure keychain, common security risks, and most importantly, how to address these risks effectively and protect our personal data. So, if you want to bolster your mobile phone security and maintain peace of mind, read on!
Inside This Article
- Keychain Security Recommendations
- Identifying Security Risks in Keychain
- Resolving Keychain Security Vulnerabilities
- Best Practices for Keychain Security
- Conclusion
- FAQs
Keychain Security Recommendations
When it comes to protecting your sensitive data on your mobile phone, keychain security is of utmost importance. The keychain is a secure storage container that helps safeguard your passwords, account credentials, and encryption keys. To ensure that your keychain is well-protected, here are some essential security recommendations to follow:
- Strong Password: Set a strong password for your keychain. Avoid using easily guessable or common passwords. Use a combination of uppercase and lowercase letters, numbers, and special characters.
- Enable Auto-Lock: Configure your device to automatically lock after a period of inactivity. This adds an extra layer of security by requiring a password or biometric verification to access the keychain.
- Two-Factor Authentication: Enable two-factor authentication whenever possible, especially for services that store sensitive data in your keychain. This adds an additional verification step, making it harder for unauthorized access.
- Regular Updates: Keep your operating system and apps up to date. Developers frequently release security patches and updates to address vulnerabilities. Applying these updates ensures that any known security issues with the keychain are patched.
- Disable iCloud Keychain: If you have concerns about the security of storing your data in the cloud, consider disabling iCloud Keychain. Storing your keychain locally can provide an extra layer of security, as it reduces the risk of unauthorized access to your data through cloud-based attacks.
- Third-Party Password Managers: Consider using third-party password managers that provide additional features and enhanced security measures for your keychain. These password managers often offer functionalities like password generation, secure syncing, and protection against phishing attacks.
- Audit Your Keychain: Regularly review the contents of your keychain and remove any unnecessary or outdated entries. This reduces the risk of exposure to compromised or outdated credentials.
- Backup Your Keychain: Regularly back up your keychain data to a secure location. This ensures that you can recover your passwords and sensitive information in case of accidental deletion or device failure.
- Public Wi-Fi Caution: Exercise caution while accessing your keychain on public Wi-Fi networks. Use a virtual private network (VPN) to encrypt your internet connection and protect your keychain from potential eavesdropping and attacks on unsecured networks.
- Education and Awareness: Stay informed about the latest security practices and threats related to keychain security. Educate yourself on common phishing techniques and social engineering attacks to avoid falling victim to such scams.
By following these keychain security recommendations, you can enhance the protection of your sensitive data, passwords, and credentials stored in your keychain. Remember, it’s essential to be proactive in safeguarding your keychain to avoid potential security risks.
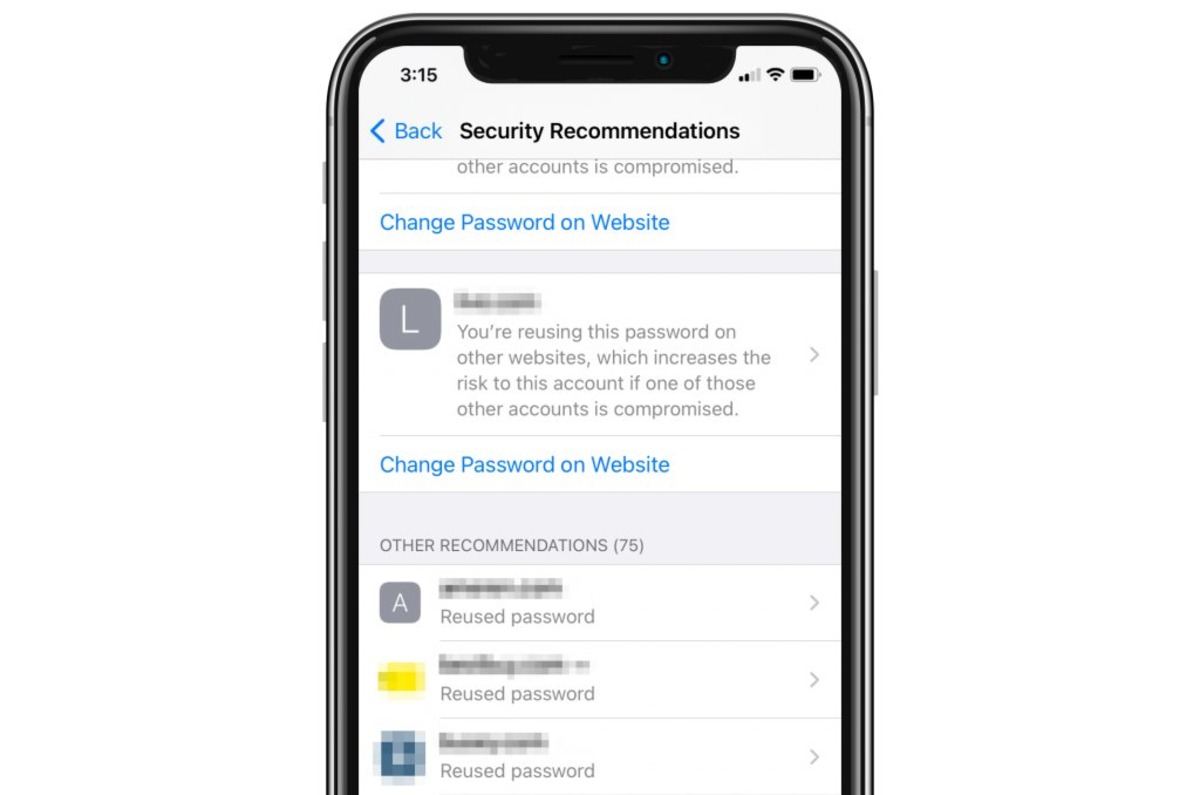
Identifying Security Risks in Keychain
Keychain security is a critical aspect of keeping your mobile phone data secure. When it comes to identifying security risks in your keychain, there are a few key factors to consider. By staying vigilant and proactive, you can ensure that your sensitive information remains protected. Here are some essential points to help you identify security risks in your keychain:
- Inactive or outdated keychain: One of the first signs of a security risk is an inactive or outdated keychain. If you haven’t updated or used your keychain for a while, it’s essential to check for any vulnerabilities that may exist.
- Unrecognized or suspicious keychain entries: Take a close look at all the entries in your keychain. If you come across any unfamiliar or suspicious entries, they could be indicators of security risks. Remove any entries that you don’t recognize or cannot trust.
- Weak password protection: Password protection is a vital layer of security for your keychain. If your keychain password is weak or easily guessable, it puts your entire keychain at risk. Make sure to use strong, unique passwords that are not easily compromised.
- Expired certificates: Certificates play a crucial role in securing your keychain, particularly for SSL/TLS connections. Check for any expired certificates and update them promptly to prevent any security vulnerabilities.
- Unauthorized access attempts: Keep an eye out for any unauthorized access attempts to your keychain. If you notice multiple failed login attempts or suspicious activity, it’s a clear indication that someone is trying to breach your security. Take immediate action to strengthen your keychain’s defenses.
Identifying security risks in your keychain is essential in order to maintain the integrity of your mobile phone’s data. By regularly reviewing and addressing any potential vulnerabilities, you can ensure that your keychain remains a secure repository for your sensitive information.
Resolving Keychain Security Vulnerabilities
Keychain is a crucial component of iOS and macOS devices, as it securely stores sensitive information such as passwords, certificates, and encryption keys. However, just like any other security feature, it’s not entirely foolproof.
If you suspect that your Keychain might have security vulnerabilities, it’s essential to take immediate action to resolve them. Here are some steps you can follow:
- Update your software: Keeping your devices up to date with the latest software version is crucial for maintaining security. Regularly check for system updates and install them to patch any known vulnerabilities that attackers might exploit.
- Secure your devices: Set a strong passcode or use biometric authentication, such as Touch ID or Face ID, to secure your device. This prevents unauthorized access and adds an extra layer of protection to your Keychain.
- Change compromised passwords: If you suspect that any of your passwords stored in Keychain have been compromised, change them immediately. Use strong, unique passwords for each service and enable two-factor authentication whenever possible.
- Remove unused credentials: Regularly review your Keychain and remove any outdated or unused credentials. This reduces the potential attack surface and minimizes the risk of exposure to vulnerabilities.
- Enable iCloud Keychain: Consider enabling iCloud Keychain, which securely syncs and stores your Keychain data across all your Apple devices. This ensures that your passwords are readily available and protected, even if you lose or replace a device.
- Use Keychain Access: Keychain Access is a utility that allows you to manage your Keychain items, view their details, and even delete or modify them if necessary. Familiarize yourself with this tool so that you can efficiently resolve any security issues that arise.
- Be cautious of phishing attempts: Be wary of phishing attempts that aim to trick you into revealing your sensitive information. Avoid clicking on suspicious links or providing your credentials on untrusted websites.
By following these best practices, you can ensure that your Keychain remains secure and protected from potential security vulnerabilities. Regularly reviewing and maintaining your Keychain’s security is essential to safeguard your sensitive information and maintain a safe digital environment.
Best Practices for Keychain Security
When it comes to protecting your digital identity, securing your passwords and sensitive information is of utmost importance. The Keychain, a built-in feature on mobile devices, offers a secure and convenient way to store and manage passwords, encryption keys, and certificates. To ensure the utmost security, it’s important to follow best practices for Keychain usage. Here are some key guidelines to keep in mind:
1. Use Strong and Unique Passwords: One of the fundamental rules of digital security is to use strong, complex passwords. Avoid using common words or personal information that can be easily guessed. Instead, opt for a mix of uppercase and lowercase letters, numbers, and special characters. Additionally, make sure each account has a unique password to minimize the risk of a single data breach compromising multiple accounts.
2. Enable Two-Factor Authentication: Two-factor authentication adds an extra layer of security to your accounts by requiring a second form of verification, such as a code generated on your mobile device. Enable this feature whenever possible, as it significantly reduces the risk of unauthorized access even if your password is compromised.
3. Regularly Update and Patch Devices: Keeping your mobile device’s operating system and apps up to date is essential for maintaining security. Developers frequently release updates that address vulnerabilities or patch security loopholes. By regularly updating your device, you ensure that you have the latest security enhancements and fixes.
4. Be Cautious of Third-Party Apps: While apps can enhance your mobile experience, it’s important to exercise caution when granting permissions and sharing data with third-party applications. Only download apps from reputable sources, read reviews, and carefully review the permissions requested by the app. Limit the access that third-party apps have to your Keychain, and regularly audit and remove any unnecessary app access.
5. Backup Your Keychain: Regularly backing up your Keychain allows you to recover your stored passwords and information in case of device loss, damage, or a need to switch to a new device. Consult your device’s settings or consult the manufacturer’s documentation to learn how to enable automatic backups or manually export your Keychain data.
6. Be Mindful of Shared Devices: If you share your mobile device with others, be cautious of storing sensitive information in your Keychain. Consider creating separate user accounts or utilizing guest modes that limit access to personal data. Avoid saving passwords or sensitive information for shared accounts in the Keychain.
7. Use a Strong Passcode or Biometric Authentication: Protect your device and Keychain access with a strong passcode or biometric authentication, such as fingerprint or facial recognition. This adds an extra layer of protection in case your device falls into the wrong hands.
8. Regularly Review and Update Keychain Entries: Periodically review the entries in your Keychain and remove any outdated or unused passwords. This ensures that only necessary and up-to-date information is stored, reducing the potential for security risks.
9. Educate Yourself About Keychain Security: Stay informed about the latest best practices and security trends related to Keychain usage. Regularly read articles, blogs, and official documentation from trusted sources to keep yourself updated on any emerging threats or recommended security measures.
By following these best practices for Keychain security, you can maintain a high level of security for your passwords and sensitive information. Remember, prioritizing the protection of your digital identity is crucial in today’s interconnected world.
In conclusion, ensuring the security of your keychain is essential to safeguarding your personal information and protecting yourself against potential security risks. By regularly checking the Keychain Security Recommendations and taking the necessary steps to address any identified issues, you can have peace of mind knowing that your data is secure. Be proactive and proactive in taking steps to fix any security risks, such as updating passwords, enabling two-factor authentication, and removing any trusted certificates or keys that pose a potential threat. Remember, staying vigilant and implementing security best practices will go a long way in keeping your personal information safe from unauthorized access. So, take the time to review your keychain security today and make the necessary changes to protect your data and maintain your online privacy.
FAQs
Q: What are Keychain security recommendations?
Keychain security recommendations are suggestions made by your device’s operating system to ensure the privacy and security of your sensitive information, such as passwords, credit card details, and other login credentials. These recommendations help you identify and fix potential security risks within your device’s keychain.
Q: How do I access Keychain security recommendations?
To access Keychain security recommendations, navigate to the settings menu on your mobile device. Look for the “Keychain” or “Security & Privacy” section and tap on it. Within this section, you should find options to view and implement the recommended security measures for your keychain.
Q: Why is it important to follow Keychain security recommendations?
Following Keychain security recommendations is vital to safeguarding your personal information from unauthorized access and potential security breaches. By implementing these recommendations, you can significantly reduce the risk of your sensitive data being compromised or stolen.
Q: What are some common security risks within the Keychain?
Some common security risks within the Keychain include weak passwords, outdated or vulnerable applications, unsecured Wi-Fi networks, and malicious apps that may attempt to access your keychain data. Keychain security recommendations help you address these risks effectively.
Q: How can I fix security risks within my Keychain?
To fix security risks within your Keychain, start by updating your device’s operating system and all installed apps to the latest versions. Ensure that you use strong and unique passwords for your accounts. Avoid connecting to unsecured Wi-Fi networks and be cautious while downloading apps from unknown sources. Following these recommendations should help mitigate potential security risks.
